In an age where online services are integral to industries, governments, and societies, cybersecurity has become one of the most pressing global concerns. With the growing reliance on digital infrastructures, Distributed Denial of Service (DDoS) attacks continue to pose a significant threat to the accessibility of critical internet services. These attacks aim to overwhelm targeted systems with traffic, causing widespread disruption. Despite advancements in cybersecurity, detecting and mitigating DDoS attacks remains one of the most challenging aspects of network security.
Addressing these challenges head-on, Himmat Rathore and his research team have introduced an innovative methodology to enhance DDoS detection using Machine Learning (ML) and Explainable Artificial Intelligence (XAI) within Software-Defined Networking (SDN) architectures. This pioneering work was presented at the 4th ASIANCON 2024, a prestigious conference held in Pune, India, on August 24th, 2024. Technically co-sponsored by the IEEE Bombay Section and sponsored by AICTE New Delhi, the event gathered experts from around the world to showcase cutting-edge technological advancements.
The conference featured a range of groundbreaking contributions, but the paper by Rathore and his team titled "An Explanatory Machine Learning Method for the Identification of DDoS Attacks in SDN Architectures" stood out for its practical applications in cybersecurity. This paper presents a revolutionary approach to DDoS detection by incorporating machine learning models that not only offer exceptional accuracy but also provide transparent, interpretable explanations for their predictions. With the research now indexed on IEEE Xplore, the visibility and impact of this work within both academic and professional communities are growing significantly.
The New Era of DDoS Attack Detection
One of the biggest hurdles in combating DDoS attacks is detecting them in real time and accurately identifying their source. Traditional detection systems struggle to keep up with the evolving complexity of these attacks, which often hide among legitimate traffic flows. Moreover, many existing solutions fail to provide adequate transparency, leaving network administrators without clear explanations for why specific detections were made. This lack of interpretability can lead to mistrust of machine-driven decisions, particularly in critical sectors.
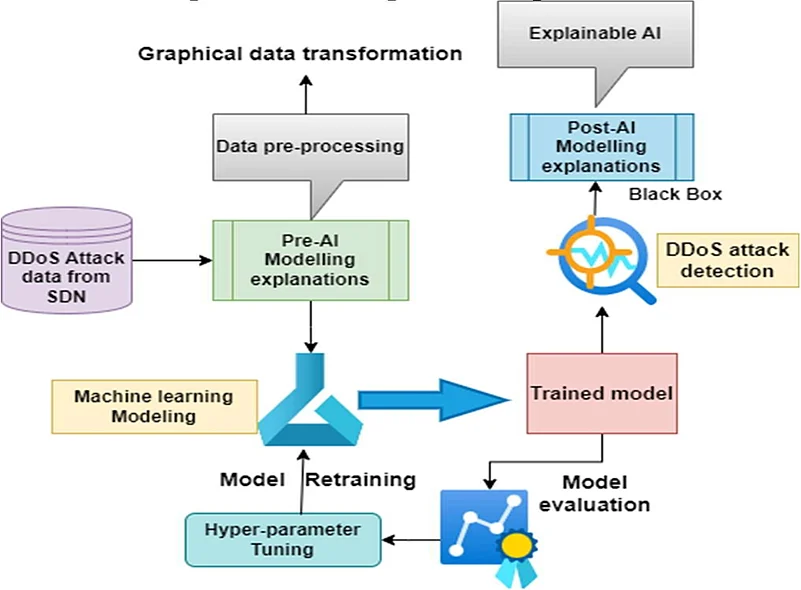
Himmat Rathore and his team aimed to overcome these limitations by developing a three-step methodology that leverages both the strengths of Software-Defined Networking (SDN) and Explainable AI (XAI). SDN allows for a flexible, centralized control of network traffic, which enhances the system's ability to detect anomalies like DDoS attacks. The innovative detection system proposed by Rathore not only improves accuracy but also brings greater transparency to the detection process, allowing IT professionals to understand the reasoning behind each decision.
Step 1: Pre-Modeling Explanations – Building Transparency from the Ground Up
The first stage of the methodology focuses on pre-modeling explanations, which involves pre-processing and analyzing raw network traffic data. A significant breakthrough here is the visual representation of data patterns, enabling security professionals to gain meaningful insights into traffic flows. This process is essential for identifying early signs of DDoS attacks by highlighting anomalies in a way that is easily interpretable by human operators.
Data pre-processing also plays a crucial role at this stage. Rathore’s team ensures the accuracy of their models by eliminating null values and transforming raw data into machine-readable formats through techniques like one-hot encoding, where string features are converted into numerical ones. This level of preparation enhances the effectiveness of the machine learning models in the subsequent stages.
By laying a solid foundation for data processing and visualization, this stage improves the overall reliability of the detection system, making it easier to distinguish between legitimate and malicious traffic.
Step 2: Machine Learning Models – Harnessing Decision Trees and Random Forests for Accuracy
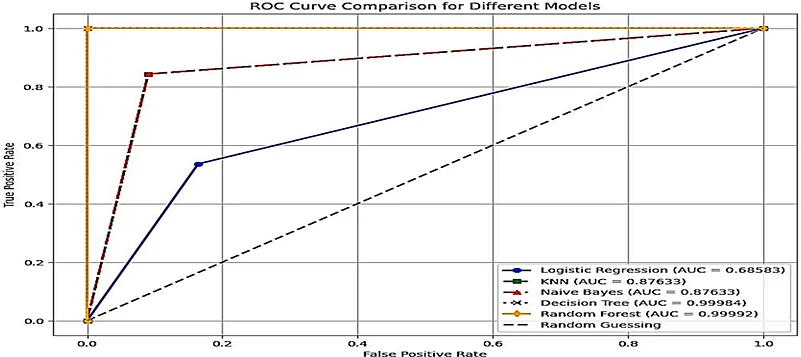
In the second stage, the focus shifts to applying machine learning algorithms to the pre-processed data. Rathore's team experimented with several ML models to determine the most effective approach for detecting DDoS attacks. Among the algorithms tested, decision tree and random forest models emerged as top performers, achieving near-perfect accuracy in distinguishing DDoS attack traffic from normal network behavior.
This level of accuracy marks a significant advancement in the field. DDoS attacks often blend into legitimate traffic, making them difficult to identify using traditional systems. However, decision trees and random forests excel at recognizing complex patterns within the data, making them ideal for this type of anomaly detection.
While achieving high accuracy is critical, Rathore's research goes beyond mere detection. The team recognized the need for transparency in the decision-making process, particularly for cybersecurity applications where understanding the "why" behind an outcome is as important as the outcome itself.
Step 3: Explainable AI – Unlocking Transparency in AI Systems
The third and final stage of the methodology brings Explainable AI (XAI) into the spotlight. While many machine learning models operate as “black boxes,” where the internal decision-making process is opaque, XAI provides insights into how and why a particular decision was made. For cybersecurity professionals, this interpretability is vital. It not only builds trust in the system but also enables them to take more informed actions based on the AI's predictions.
Rathore’s approach combines high accuracy with XAI, ensuring that network administrators are not left guessing why a detection was flagged as a DDoS attack. By providing clear, interpretable explanations, the system fosters greater confidence in the decision-making process and allows for quicker, more precise responses to potential threats.
This innovation addresses a major gap in the current cybersecurity landscape. Traditional machine learning models often leave users in the dark regarding the factors behind a detection, making it difficult to adjust or refine systems as needed. With XAI, Rathore and his team have brought a new level of transparency to the table, creating a solution that is both highly effective and user-friendly.
Real-World Applications and Future Impact
The practical implications of this research are far-reaching. The proposed system can be implemented in real-time to enhance the ability of organizations to detect and mitigate DDoS attacks before they cause significant disruptions. The combination of high accuracy from machine learning models and transparency from XAI ensures that the system is not only reliable but also understandable to the professionals who rely on it.
Beyond DDoS detection, this methodology has the potential to be applied to other areas of cybersecurity, such as malware detection, insider threat identification, and IoT security. The ability to offer transparent explanations for AI-driven decisions will become increasingly important as more industries adopt AI for critical applications.
Pioneering a New Frontier in Cybersecurity: Himmat Rathore’s Lasting Impact
Himmat Rathore's work in the field of cybersecurity goes far beyond this groundbreaking research. As a Technical Leader at DISYS Solutions Inc. (dba DSI Tech) in the United States, Rathore has led numerous high-value network security projects, significantly impacting both the public and private sectors. His contributions have helped shape the way organizations approach cybersecurity, particularly in areas like Managed Services and large-scale network infrastructure.
Rathore’s impressive credentials, including five Cisco Certified Internetwork Expert (CCIE) certifications, place him among an elite group of professionals globally. His deep understanding of networking and security, coupled with his leadership in driving large-scale initiatives, has earned him recognition as a key figure in the cybersecurity industry.
Under his leadership, DISYS Solutions Inc. has expanded its cybersecurity and Managed Services capabilities, offering robust solutions that address both immediate threats and long-term security challenges. Rathore’s ability to integrate cutting-edge technology with real-world applications continues to push the boundaries of what is possible in cybersecurity.
In sum, Himmat Rathore’s contributions to the field, exemplified by his innovative approach to DDoS detection, are shaping the future of cybersecurity. His work is not only advancing the technical capabilities of network security but also promoting a deeper understanding of how AI and machine learning can be used transparently and effectively. As the digital landscape continues to evolve, Rathore’s leadership and vision ensure that the future of cybersecurity is in capable hands.